What is Mobile Device Management & how does it work?
What is Mobile Device Management & how does it work?
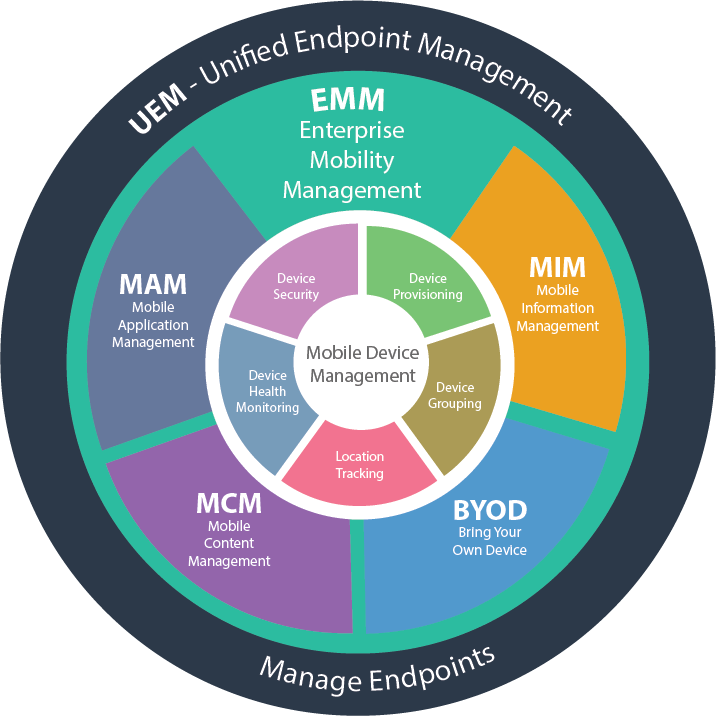
What is an MDM? Mobile Device Management alludes to any instrument or programming intended to help IT chairmen control and secure cell phones like cell phones and tablets over an association. MDM is a significant piece of big business portability to the executives and endpoints the executives, particularly as more organizations receive Bring Your Own Device strategies that permit representatives to get to organization information, records, and applications on their own gadgets.
How does MDM work?
At the point when an IT administrator needs to design a cell phone on an organization arrangement, the administrator inputs the new strategy on the MDM server’s administration support.The server then pushes the change to the MDM operator, which applies the changed arrangement to the cell phone through that gadget’s work in APIs. IT divisions can likewise utilize this MDM server-specialist association with convey and control applications on oversaw gadgets.
What are the advantages of MDM?
The most significant advantage of cell Mobile Device Management is data security. Cell phone the board secures organization information through gadget level strategies given by the gadget producer or stage supplier. With the assistance of these strategies, IT managers can control, secure, and detach cell phones from organization systems. For instance, MDM permits IT to empower gadget wide encryption and naturally lock or wipe a gadget on the off chance that it is lost or taken.
MDM can likewise encourage portable application of the board by making it simpler for IT chairmen to send, design, and update versatile applications on organization gadgets or individual worker gadgets. This disentangles IT the board of each cell phone with access to an association’s system. Other famous highlights of MDM incorporate cell phone stock and following, secret phrase requirement, whitelisting and boycotting certain applications, and information encryption authorization.
Mobile Device Management Solutions:
Most cell Mobile Device Management arrangements furnish associations with start to finish security — which means the versatile applications, system and information utilized by the cell phone (notwithstanding the cell phone itself) are overseen by an association’s IT office with a solitary cell phone programming item.
Some undertaking MDM arrangements consolidate portable security and cost the executives in a solitary item. Contingent upon the merchant and what explicitly highlights it underpins, you can ordinarily expect cell phone programming to contain a few or the entirety of the accompanying highlights: the board and backing of versatile applications, portable strategy the board, stock administration, security the executives and telecom administration the executives.
BYOD and Mobile Device Management
The across the board expansion of consumerization of IT implies progressively close to home customer processing gadgets —, for example, cell phones, workstations and tablets — are brought to the working environment by representatives for use and availability on the corporate system. The expression BYOD (bring your own gadget) has gotten broadly embraced to allude to these workers. The present class of cell Mobile Device Management programming is one way that an association can convey secure versatile answers for its BYOD workforce.
How does cell Mobile Device Management fit into my IT technique?
On the off chance that your workers use workstations, cell phones, tablets, or whatever other cell phone that approaches your organization’s records or information, cell Mobile Device Management is fundamental. Without MDM set up, a solitary lost cell phone with access to your system can turn into a significant security issue. On the off chance that this gadget approaches private client data (like individual clinical data or Visa numbers) you could be confronting exorbitant charges and claims identified with consistency infringement.
MDM secures you by permitting your IT administrator to remotely secure or wipe a missing cell phone from your office. MDM additionally makes it simpler to actualize vast updates to business applications or gadget approaches by pushing them from the MDM server.
Key components of a MDM arrangement include:
Resource the executives, which incorporates multi-stage support for organizations to apply custom hierarchical approaches to big business versatility and BYO gadget use in the corporate system. Resource executives may screen and control how the gadgets can be utilized just as the organization approaches over completely enlisted gadgets, numerous stages, and working framework renditions.
Designs the executives, which can recognize, control, and oversee equipment and programming settings dependent on geographic locales, client profiles, and personality.
Hazard the executives, reviews, and announcing, which screens gadget action and reports bizarre conduct to restrain issues, for example, unauthorized access of corporate systems or information moves.
Programming updates and appropriation, which can remotely control applications, programming and OS updates, and licenses over different gadgets.
Profile the executives, which permits the board of arrangements and settings to explicit gatherings of end clients dependent on explicit profiles.
Character and access the executives, which guarantees that the gadget, information, arrange association, and administrations are given to proper approved clients.
Applications the executives, which disperses, oversees settings, and dark and whitelists applications and programming usefulness.
Undertaking application stores, which keep up a library of applications and administrations devoted for corporate utilize that are accessible to approved end-clients.
Transmission capacity enhancement, which oversees data transfer capacity use at the gadget and application level.
Information security, which guarantees that information is gotten to, moved, and used as per hierarchical strategies. For example, in occasion of gadget burglary or misfortune, information put away on the gadget can be cleared out remotely.
Content administration, which synchronizes and makes sure about business data over different gadgets.
Technical support, which incorporates committed remote innovation backing can be given remotely.
Table of Contents








